NFC Reading
DOT NFC is a mobile library (both for Android and iOS) enabling the reading of data from the RFID chip contained in the eMRTD with NFC-enabled smartphone.
Electronic Machine Readable Travel Document - eMRTD
The MRTD is specification of an official travel document. It contains in a standardized format, various identification details of the holder, including a photo (or digital image) with mandatory and optional identity elements. The mandatory elements, apart from the photo, are reflected in a two- or three-line machine readable zone (MRZ).
The eMRTD contains a NFC-readable RFID chip. This chip stores data from the travel document data page and the mandatory biometric data of the holder: the photograph. The data is organized in data groups (DG1, DG2, SOD, etc.).
As the chip contains digitally signed data, a country issuing an eMRTD has to maintain a dedicated public key infrastructure (PKI). The “Root” of this PKI is the Country Signing Certification Authority (CSCA). The document signer (DS) certificate, signed by the CSCA, proves the authenticity and integrity of the data on the chip and the link to the issuer.
Specifications and standards of eMRTD can be found in ICAO Document 9303.
Access Control
In order to read the content of the eMRTD chip, Access Control has to be established. Access Control mechanism ensures that the data from the eMRTD chip is not read without attention of the ID document holder.
ICAO defines two protocols for Access Control:
- BAC - Basic Access Control
- PACE - Password Authenticated Connection Establishment
Both Access Control protocols use access keys generated from MRZ - MRZ Key. The MRZ Key is created from document number, date of birth and date of expiry which are present in the MRZ, see image below.
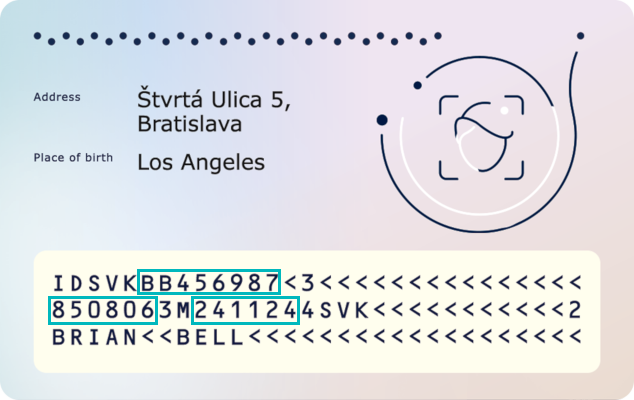
After the Access Control has been established, chip will provide access to less sensitive data groups.
Data Groups and Elements in eMRTD
The standard Access Control enables to read these data groups:
| Data group | Description |
|---|---|
| DG1 | Personal details recorded in MRZ as text data |
| DG2 | Face photo image |
| DG7 | Signature of document holder as image |
| DG11 | Additional personal details as text data |
| DG12 | Additional document details as text data |
| DG13 | Optional details as binary data |
| DG15 | Active Authentication Public Key Info |
| SOD | Document Security Object |
The list of all possible data groups is below. Note, that the fields DG3 and DG4 cannot be read without additional certificate.
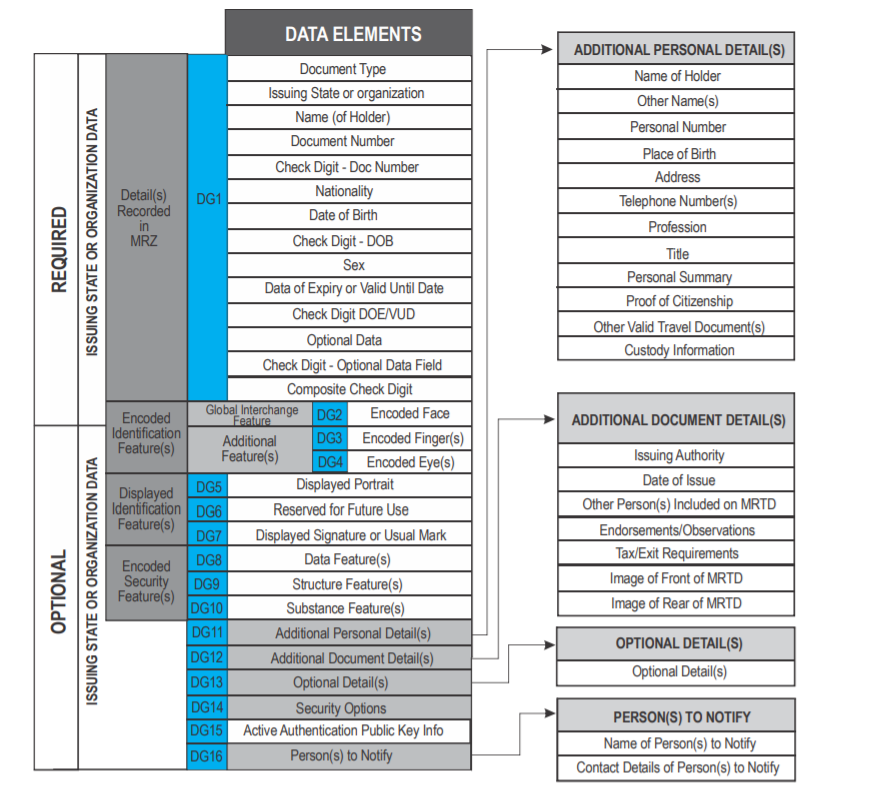
Authentication of eMRTD Chip
After the Access Control has been established, authenticity of the data stored in the chip can be verified. This is the most reliable method to check ID document authenticity using a smartphone.
Two ICAO defined authentication protocols are implemented:
- Passive Authentication (proves that the data in the document have not been modified)
- Active Authentication (proves that data haven’t been copied to an RFID carrier different from the original ID document)
Passive Authentication
The Passive Authentication protocol verifies that the contents of the Document Security Object (SOD) and data groups are authentic and not changed. It does not prevent copying of the chip content or chip substitution.
Passive Authentication has following steps:
- extract Document Signing Certificate from the chip
- validate Document Signing Certificate with CSCA Certificates provided in the master list
- verify that Document Security Object (SOD) has been correctly signed by Document Signing Certificate
- verify that the contents of the data groups are authentic and unchanged by hashing the contents and comparing the result with the corresponding hash value in the Document Security Object (SOD).
Master List
Note: Innovatrics does not provide its customers with certificates for Passive Authentication. It is a responsibility of integrator to acquire the certificates needed, either from ICAO organization, or from country’s governmental organizations. The benefit of this is that the integrator gets notified about the new certificate updates.
In order to authenticate the eMRTD chip with Passive Authentication, the library needs a master list containing CSCA certificate chain, which was used to sign the Document Signing Certificate present on the chip. This master list has to be in PEM file format.
Many countries provide their certificates in the ICAO Public Key Directory. It is currently possible to retrieve suitable master list from there (after accepting the Terms & Conditions). Search for “The latest collection of CSCA Master Lists”. However, this master list is in LDIF file format (and 5 MB big), so the certificates need to be converted to PEM file format. In case that support for only some countries is needed, the required certificates cane be filtered from this file to keep app size smaller.
These resources can help converting LDIF file to PEM file:
Active Authentication
The Active Authentication protocol verifies that the chip data has been read from the genuine chip, stored in the genuine eMRTD. It prevents usage of a copied chip content or a chip substitution.
Active Authentication has following steps:
- generate random challenge
- request signature for this challenge from the chip
- verify signature using public key stored in Data Group 15 (DG15)
DOT NFC
DOT NFC library provides simple non-UI component - NFC Document Reader which facilitates the NFC reading process. It takes MRZ Key as an input and returns the result object as the output. If Passive Authentication protocol is needed, the master list also needs to be provided as an additional input.
The process contains the following steps:
- Access Control establishment - In order to access data groups on the chip, NFC Document Reader will execute PACE first. If it fails or it is not supported, NFC Document Reader will execute BAC.
- After the Access Control has been established, the available data groups will be read.
- Then, NFC Document Reader will try to authenticate the chip using Active Authentication and Passive Authentication.
- Lastly, NFC Document Reader will return the result object containing: (1) the data from data groups, (2) entries indicating success or failure of authentication protocols.